Cybersecurity Bulletin - The Big Phish
11/8/20, 5:04 pm
What's been going on out there?
The Big Phish! Phishing emails relating to the COVID-19 virus have reigned supreme. Though merely emails these aren’t to be taken lightly as a single click of a malicious link, opening a malicious attachment or responding with details about yourself or your company where belief in the recipient’s legitimacy as a business contact can cause much damage to yourself, your company and their reputation.
COVID-19 has given cyber attackers a new frontier to prey upon. The NEC Australia Security Operations Centre (SOC) has been put into 6th gear since lockdown, watching, analysing, and detecting any suspicious or malicious activities seen across the NEC corporate network.
The SOC has been hard at work configuring new ways to detect the plethora of new threats the world is now facing since the pandemic fell upon us all. Phishing scams, malicious email attachments and links, website spoofing are just some of what we are seeing in this new climate. Luckily with the cyber security teams across the world sharing their findings we have the “indicators of compromise” (IOC)* to thwart many of them. Sure, these things are happening all the time but since the recent COVID-19 pandemic they have all increased exponentially meaning the team has had to be more focused than ever.
*Indicators of Compromise (IOC) are the evidence (or artefacts) observed and reported by cyber communities (government, cyber security businesses, individuals working in the area of IT inside a company) that point to high confidence malicious activity on systems and/or networks. IOCs are typically IP addresses, URLs, domains, virus signatures, and file hashes (unique file value that corresponds to its contents – malicious in this case).
Here are a few examples of what’s been going on out there:
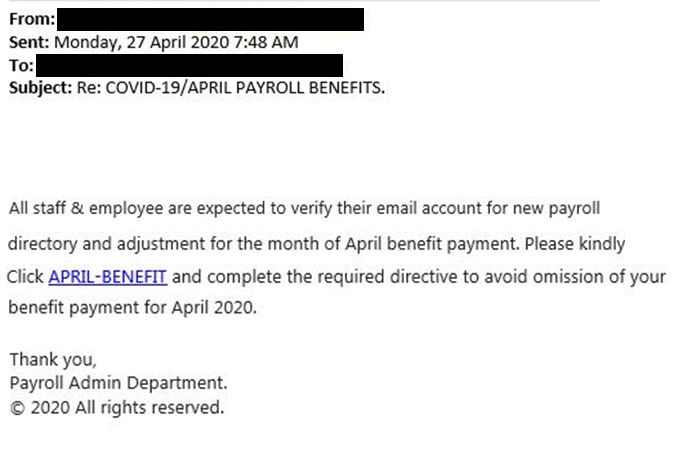
Fake payroll scam
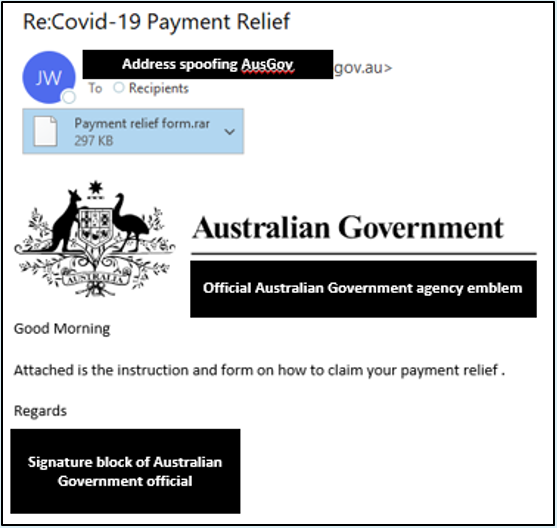
Fake ATO tax credit scam
There have also been several SMS phishing attempts:
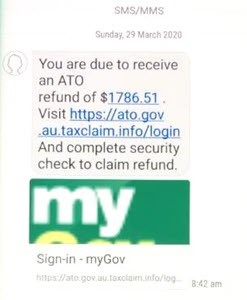
Fake myGov tax refund SMS
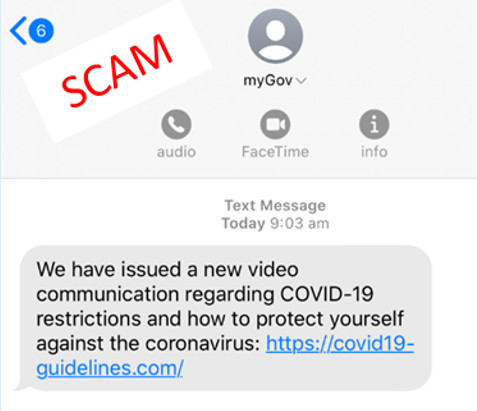
Fake myGov COVID-19 SMS
Help Desk and E-mail Scams
Australians have been experiencing IT help desk scams that pretend to come from their employer. Since the rise in working from home, scammers are focusing attention on these areas for a quick gain. Their targets have been confidential data, money or just fun. In this instance, recipients are receiving emails to log into their company portal. If successful, the scammers gain company credentials for logging onto systems.

Another COVID-19 phishing campaign has also been on the rise. It installs software known as the “NetSupport Manager” remote administration tool, known otherwise as a RAT. The attack begins as a phishing email from the “John Hopkins Center”, a reputable organisation sharing up-to-date coronavirus related statistics.

The attachment is where things get interesting. The Excel file contains what seems to be harmless yet interesting stats of, in this case, US coronavirus statistics.

However, this spreadsheet hides malicious macros that prompt the user to “Enable Content”. Once clicked, the “NetSupport Manager” client is downloaded and installed. After installation, the threat actor has full control over the device and can execute commands, exfiltrate data and cause a lot of damage.
The NEC SOC team actively hunt for inbound COVID-19-related scams. Advanced cyber security products like a Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR) platform, do a great job in identifying and mitigating these types of threats. But technology does not guarantee that a threat may slip under the radar. This is where security awareness is most important. NECs security awareness is growing with more employees reaching out to our SOC team for vetting potential phishing email scams before taking any action themselves.
Tips for Security Awareness
Question everything you receive via email and text. Did you expect to receive that email? Did you provide the sender with your mobile number? Why are you receiving an attachment from the tax office instead of a prompt to log onto your own account? Be vigilant as you could fall victim. If you are unsure of a message or email, use Google search to see if anyone else has received the same. Find reported phishing attempts at Scam Watch. Additionally, cyber.gov.au has helpful information on the topic.
How does the NEC SOC fight back?
One word, visibility. The NEC SOC Security information and event management (SIEM) platform collects thousands of events per second, 24-hours a day, 7-days a week. This includes logs from all major connectivity and security devices, endpoint management consoles, directory services and so on. SIEM consumes a wealth of data to use against leading security vendors, third-party threat intelligence feeds and in-house created use cases for detecting suspicious and malicious intent.
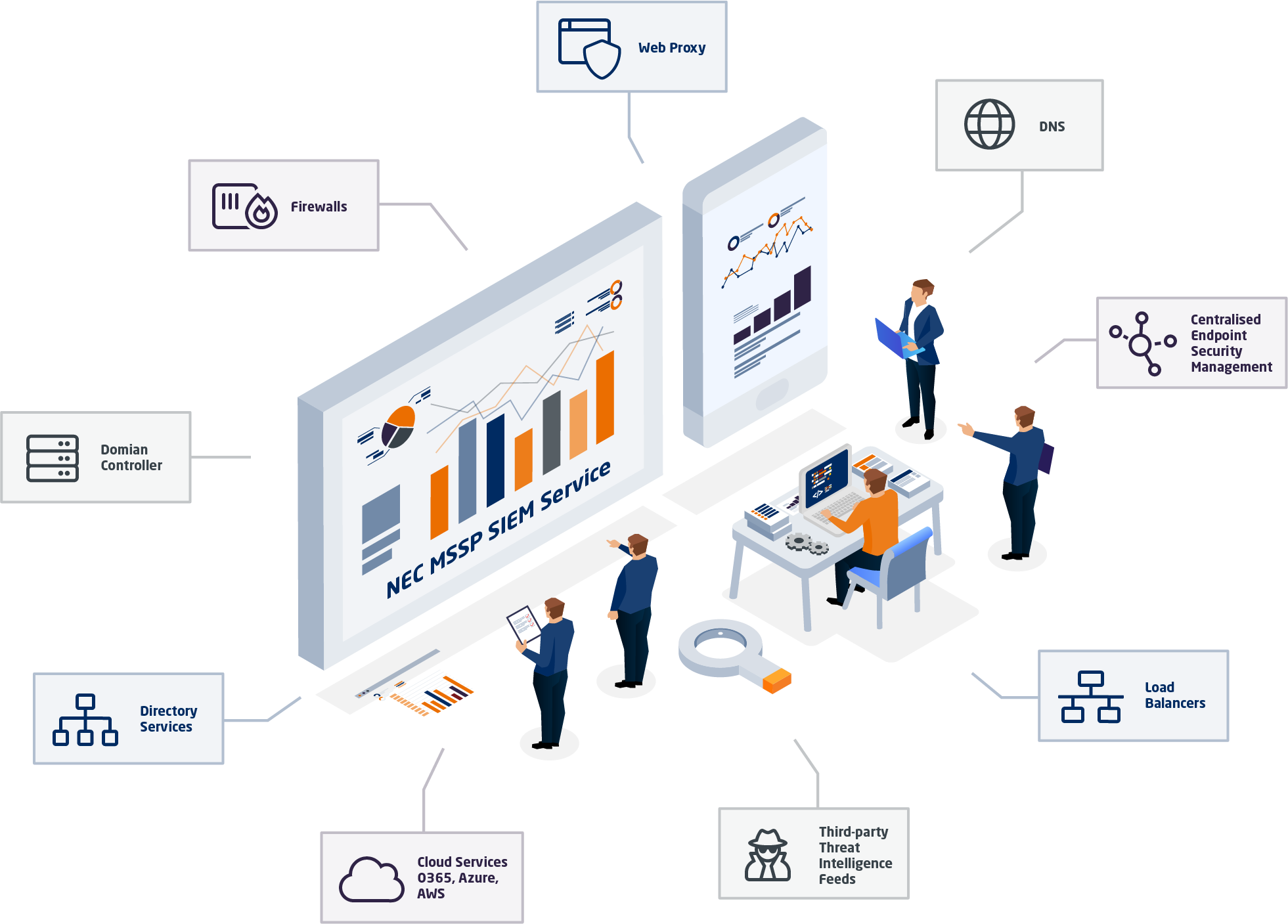
The NEC SOC analysts continuously review events via custom made dashboards that collate and categorise inbound logs. They conduct daily scans for the latest threats through the SIEM platform. Watchlists and correlation rules to monitor for all known Indicators of Compromise (IOC). The team creates new rules with advanced logic to seek out activity that could lead to malicious actions. Alerts and alarms trigger when an event matches known threats, wasting little time in eliminating it. The platform measures environmental activity and watches for anything that does not look like how it should, compared to historic data for example.
Visibility is key in any network environment and should be taken seriously. Without it there is no knowing what could be going on in the background and what repercussions there may be thereafter. Would you give up visibility of your bank account activity?
Working from home comes with risks
The pandemic brought in the new era of working from home and with that came many challenges. We all now use our own internet providers to reach all the websites and download files for work. Not all companies are equipped to monitor such activity. Depending on your company’s security posture, working from home may allow you to browse websites considered “Not Suitable for Work” (NSFW). Venturing down the line of unrelated work browsing is a potential problem. This may expose the whole company to many risks.
Personal email can be a big risk. Opening attachments without thought of how trustworthy the sender is; emailing work data using a personal account; situations like these happen whether the user is aware of the risks or not.
The use of personal storage devices and peripherals on work laptops can also pose a risk. When was the last time you scanned your USB drive for viruses? A simple virus attached to that “chrome.exe” installation file you put on your partner’s computer could have been compromised. Only connect devices that have been properly controlled to any laptop.
Remember to lock your computer. Anyone can make the simple mistake of leaving their laptop unlocked but this is something to get into the habit of, even at home. There are plenty of random scenarios where having a laptop unlocked can be enticing at the right moment: children playing, family members wanting to look something up on the internet, your partner loading up a family video from a USB stick. Locking the computer can prevent much damage whether the loss of files, a mistaken email sent to the boss, or the accidental sharing of confidential information. Some information may be for your eyes only, especially if you require a security clearance. Get in that habit – lock it (Windows Key + L or Command + Control + Q on a Mac).
Always think, could something bad happen if…? Be security aware.
So, what can we do?
It’s easy to fall into a habit of using your work laptop for all your internet needs. It is right there on the desk after all. Why not browse some unrelated work websites? Open some personal emails? Share content with friends over Facebook messenger, and download some cool new software? As we all should be aware by now, any of these actions will pose a risk to your company. While we have endpoint protection platforms, we cannot 100% rely on them. We have to rely on ourselves to do the right thing. Personal internet activities are better off done on your own personal device. This will reduce the risk of anything affecting your work laptop and the company network.
If we can control ourselves from using work resources for personal tasks, we will never be the cause of a security incidents on our corporate network. Be security conscious with incoming emails, no matter how legitimate they may seem. Question yourself. Do you know the sender? Is the sender's email address correct compared to previous emails? Should I be receiving an attachment from this person? Should I check with the sender to see if this is actually them reaching out? Be vigilant!
In the heat of the COVID-19 pandemic, bad actors take advantage of people’s kindness. Not all charities and supporting businesses are what they seem. Use Google to find information before committing to anything. Otherwise, contact your company’s security team or provider.
Stay safe out there.

Jason Gilliham
Cyber Security Lead, Security & Compliance
jason.gilliham@nec.com.au