How behavioural analytics is identifying cyber threats
15/3/23, 9:00 am
Your existing security solution may not be enough to provide business resilience amid the new threat landscape. To identify blind spots, and keep their organisation protected, forward-thinking IT security departments are embracing a behavioural analytics approach.
What is behavioural analytics, and how can it bolster your security?
A behavioural analytics solution continuously monitors the behaviour of users and devices, establishing a baseline of what normal behaviour for each of them looks like. Whenever new activities occur, your behavioural analytics solution will compare them to the baseline, and if it detects abnormalities, score them accordingly.
Here is how to integrate behavioural analytics in your security workflows to detect insider threats and lateral movement.
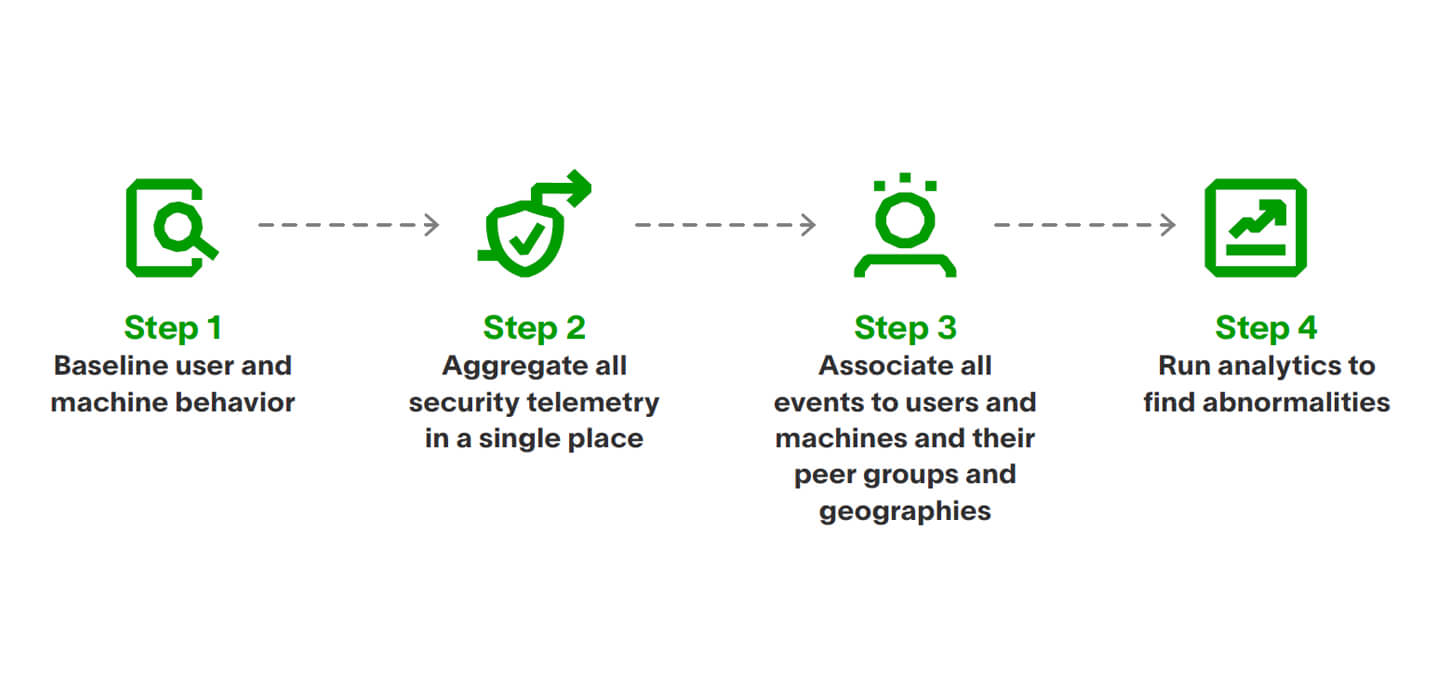
Behavioural analytics works by detecting abnormal behaviour, rather than being trained to recognise previous attacks (a rules-based approach).
As a result, it can help detect previously unknown threats. Behavioural analytics is superior for catching threats from malicious or compromised insiders, as those users who deviate from their typical behaviour in order to attack.
One excellent use of behavioural analytics is to help automate triage alerts. According to Ponemon, analysts spend 36% of their time triaging alerts.
They must take the time to answer various basic questions about an alert before deciding how to proceed. Even a single alert can trigger an avalanche of questions.
Automating your triage alerts takes that time consuming work off analysts’ hands, and behavioural analytics helps you get there. Behavioural analytics can provide insightful context for triage alerts, offering information on what normal behaviour looks like and how risky a particular anomaly is, enabling analysts to make a quick decision.
You can also automate investigations using the context provided by behavioural analytics, which links changes in behaviour back to specific users and devices, creating the opportunity to proactively automate specific, course-correcting, next steps.